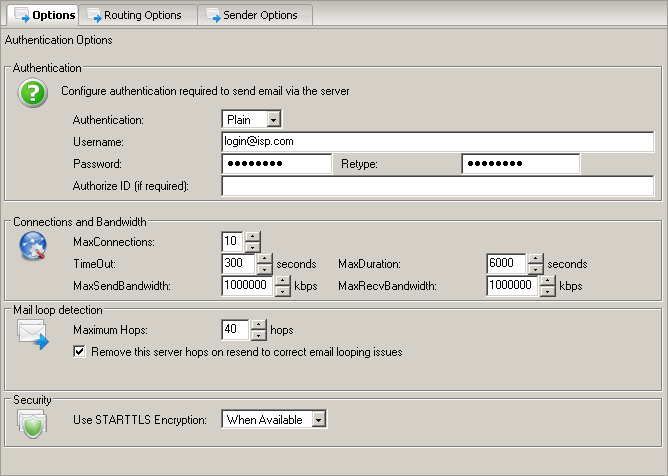
Authentication
Authentication Options
Authentication
Secure Authentication
This restricts the AUTH mechanisms that are allowed for clients connecting over unencrypted channels.
Some AUTH mechanisms transmit passwords in an insecure way. You can restrict these mechanisms to only be allowed over
secured channels such as SSL or TLS

On/Off
false
Allowed Methods
This restricts the AUTH mechanisms that are allowed for clients. It requires a service restart to change the available mechanisms.
Note DIGESTMD5 is now obsoleted by RFC5802 - Salted Challenge Response Authentication Mechanism (SCRAM) with reasons mentioned in RFC6331

On/Off
PLAIN,LOGIN,NTLM,CRAMMD5
PLAIN+NTLM
Password Hacking
Action to take
You can automatically close the connection and optionally block the IP for clients that fail authentication
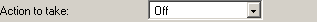
Off, Close Connection, Block IP
Off




